Adakalanya kita harus waspada terhadap serangan netcut dan virus di dalam jaringan lokal yang kita miliki, karena netcut dan virus bisa bikin sobat kerepotan.
Bagi sobat yang sudah menggunakan mikrotik, berikut adalah settingan firewall pada mikrotik untuk menangkal netcut dan drop beberapa virus.
1. Langsung saja masuk mikrotik sobat dengan menggunakan winbox atau pake putty, kemudian saya sekarang pakai winbox, untuk winbox sendiri sobat bisa dapat di postingan yang sebelumnya saya posting.
2. Langkah selanjutnya pilih
New Terminal.
3. Kemudian copy skript di bawah ini dan paste in ke
Terminal yang tadi di buka.
/ip firewall filter
add action=accept chain=input \
disabled=no dst-port=8291 protocol=tcp
add action=drop chain=forward \
connection-state=invalid disabled=no
add action=drop chain=virus disabled=no \
dst-port=135-139 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1433-1434 protocol=tcp
add action=drop chain=virus \
disabled=no dst-port=445 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=445 protocol=udp
add action=drop chain=virus disabled=no \
dst-port=593 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1024-1030 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1080 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1214 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1363 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1364 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1368 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1373 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=1377 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=2745 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=2283 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=2535 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=2745 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=3127 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=3410 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=4444 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=4444 protocol=udp
add action=drop chain=virus disabled=no \
dst-port=5554 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=8866 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=9898 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=10080 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=12345 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=17300 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=27374 protocol=tcp
add action=drop chain=virus disabled=no \
dst-port=65506 protocol=tcp
add action=jump chain=forward \
disabled=no jump-target=virus
add action=drop chain=input \
connection-state=invalid disabled=no
add action=accept chain=input \
disabled=no protocol=udp
add action=accept chain=input \
disabled=no limit=50/5s,2 protocol=icmp
add action=drop chain=input \
disabled=no protocol=icmp
add action=accept chain=input \
disabled=no dst-port=21 protocol=tcp
add action=accept chain=input \
disabled=no dst-port=22 protocol=tcp
add action=accept chain=input \
disabled=no dst-port=23 protocol=tcp
add action=accept chain=input \
disabled=no dst-port=80 protocol=tcp
add action=accept chain=input \
disabled=no dst-port=8291 protocol=tcp
add action=accept chain=input \
disabled=no dst-port=1723 protocol=tcp
add action=accept chain=input \
disabled=no dst-port=23 protocol=tcp
add action=accept chain=input \
disabled=no dst-port=80 protocol=tcp
add action=accept chain=input disabled=no \
dst-port=1723 protocol=tcp
add action=add-src-to-address-list \
address-list=DDOS address-list-timeout=15s \
chain=input disabled=no dst-port=1337 protocol=tcp
add action=add-src-to-address-list \
address-list=DDOS address-list-timeout=15m \
chain=input disabled=no dst-port=7331 \
protocol=tcp src-address-list=knock
add action=add-src-to-address-list \
address-list="port-scanners" \
address-list-timeout=2w chain=input \
comment="port-scanner" \
disabled=no protocol=tcp psd=21,3s,3,1
add action=add-src-to-address-list \
address-list="port-scanners" \
address-list-timeout=2w chain=input \
comment="SYN/FIN" disabled=no \
protocol=tcp tcp-flags=fin,syn
add action=add-src-to-address-list \
address-list="port-scanners" \
address-list-timeout=2w chain=input \
comment="SYN/RST" disabled=no \
protocol=tcp tcp-flags=syn,rst
add action=add-src-to-address-list \
address-list="port-scanners" \
address-list-timeout=2w chain=input \
comment="FIN/PSH/URG" disabled=\
no protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list \
address-list="port-scanners" \
address-list-timeout=2w chain=input \
comment="ALL/ALL scan" disabled=no \
protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
add action=add-src-to-address-list \
address-list="port-scanners" \
address-list-timeout=2w chain=input \
comment="NMAP" disabled=no \
protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
add action=accept chain=input \
comment="ANTI-NETCUT" disabled=no dst-port=\
0-65535 protocol=tcp \
src-address=61.213.183.1-61.213.183.254
add action=accept chain=input \
comment="ANTI-NETCUT" disabled=no \
dst-port=0-65535 protocol=tcp \
src-address=67.195.134.1-67.195.134.254
add action=accept chain=input \
comment="ANTI-NETCUT" disabled=no \
dst-port=0-65535 protocol=tcp \
src-address=68.142.233.1-68.142.233.254
add action=accept chain=input \
comment="ANTI-NETCUT" disabled=no dst-port=\
0-65535 protocol=tcp \
src-address=68.180.217.1-68.180.217.254
add action=accept chain=input \
comment="ANTI-NETCUT" disabled=no \
dst-port=0-65535 protocol=tcp \
src-address=203.84.204.1-203.84.204.254
add action=accept chain=input \
comment="ANTI-NETCUT" disabled=no \
dst-port=0-65535 protocol=tcp \
src-address=69.63.176.1-69.63.176.254
add action=accept chain=input \
comment="ANTI-NETCUT" \
disabled=no dst-port=0-65535 protocol=tcp \
src-address=69.63.181.1-69.63.181.254
add action=accept chain=input \
comment="ANTI-NETCUT" \
disabled=no dst-port=0-65535 protocol=tcp \
src-address=63.245.209.1-63.245.209.254
add action=accept chain=input \
comment="ANTI-NETCUT" disabled=no dst-port=\
0-65535 protocol=tcp \
src-address=63.245.213.1-63.245.213.254
4. Kemudian seteh selesai di copy/paste, sobat tinggal
reboot mikrotik sobat.
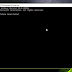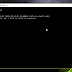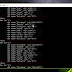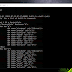
5. Setelah selesai rebot masuk kembali ke mikrotik dan buka
IP - Firewall , jika berhasih maka akan nampak seperti gambar di bawah ini
Sekian sobat postingan saya kali ini semoga bermanfaat bagi sobat semua, dan tentunya jangan malu untuk ninggalin pesan/Comment.









![Cara menghilangkan “[.ShellClassInfo] LocalizedResourceName=@%SystemRoot%\System32\Shell32.dll,-21787″](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiQN6oeHy0RzR7dcujduVxHa1tqtjqMT1S9trIJLcwzyUF_x6RyKuFvzYquTgMUCc_OF4Wl5p8dhuJxRzvlBmTyJGBxnBeoVtj2f5WHUarBRj6JQQlX_NswLarEi0QGrCUBpuUZ9b68ni5r/s72-c/unduhan+%25281%2529.jpg)


No comments:
Post a Comment